A cipher is a secret code. Today, online communications often use sophisticated algorithms to encrypt messages and data. In the past, ciphers provided a way to write a secret message that only the sender, receiver, and a small group of people in their circle knew. The Masonic Cipher, known more commonly as the Pigpen Cipher, is seldom used today but still remains a part of Freemasonry’s rich history. Read on to learn of its possible origins and how it can be deciphered.
What is a Cipher?
Ciphers are algorithms for encrypting and decrypting data. They operate symmetrically with two types of transformation: transposition and substitution. Transposition ciphers keep all the original bits of data but mix their order, and substitution ciphers replace specific data sequences with other specific data sequences. All ciphers use a system of fixed rules (algorithms) to transform a legible message into what looks like a random string of characters. Without the key, they’re impossible to decipher. It’s actually more crucial to keep the key hidden than the cipher itself.
There are many types of historical ciphers, including the Caesar Cipher, Atbash Cipher, Simple Substitution Cipher, Vignère Cipher, and Homophonic Substitution Cipher. Read more about these historical ciphers here.
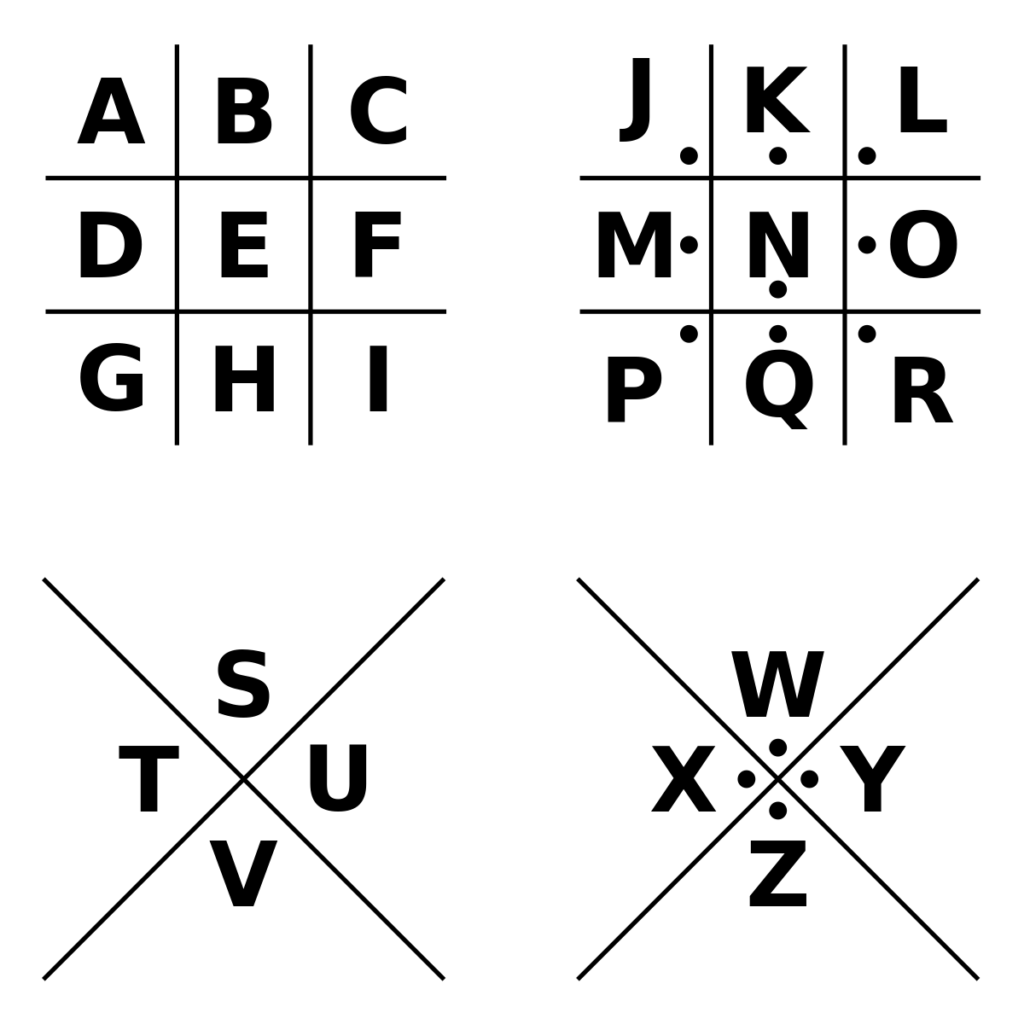
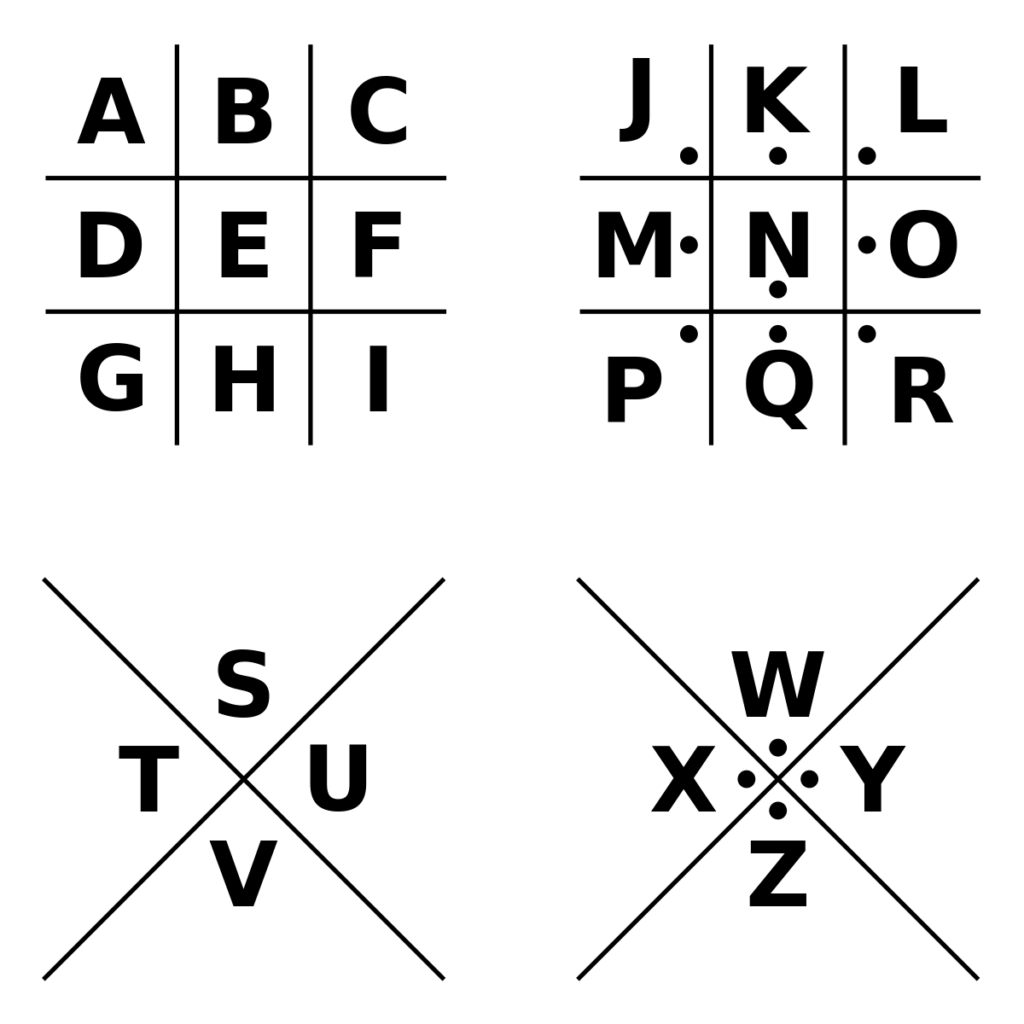
The Masonic Cipher is a geometric simple substitution cipher, which exchanges letters for symbols to create encrypted messages and consists of a 26-character key which replaces every character in the alphabet with a different symbol. In history, it’s been referred to as the Pigpen Cipher, Masonic Cipher, Freemason’s Cipher, Napoleon Cipher, Tic-Tac-Toe Cipher, and more.
Origins of the Masonic Cipher
While its true origins are unknown, it’s believed to have originated with Hebrew rabbis in ancient times; there is also evidence of the Knights Templar using one during the Christian Crusades in the Middle Ages. It’s known to have disappeared until the 18th century when some Freemasons used the cipher to keep records and rites private, and for correspondence between lodge leaders or brothers. One can sometimes see ciphered messages engraved on the tombstones of Freemasons; this cipher was also used during the Civil War by Union prisoners to communicate in Confederate prison camps.
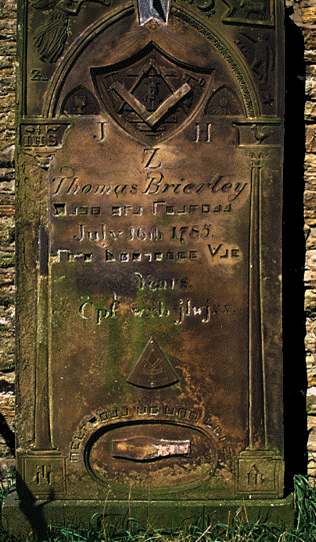
How It Works
The core elements of this system are the grid and dots; some feature X’s, like the image above. There are many variants of this cipher, who’s structure and elements are the same, but feature different symbols. Each occurrence of a letter is replaced with a designated symbol, with each symbol assigned to the letters with a key. See the example below of how you can unlock a message using one iteration of the Masonic Cipher.
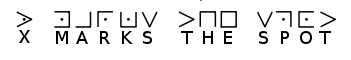
The Masonic Cipher and Pirates
According to legend, in 1730 when the pirate Olivier Levasseur was hanged, he ripped his necklace off and threw it into the crowd, crying out about a secret treasure. The necklace supposedly contained a 17-line Masonic (Pigpen) Cipher. Unfortunately, when decrypted, the note revealed to be a jumbled message in French that did not allude to any treasure, but possibly for an ancient traditional folk remedy or spell.
Ciphers Today
While today ciphers aren’t used in secret messages or in pirate treasure maps, they are very crucial in securing online communications. They are also used in Virtual Private Networks (VPNs) to connect remote workers or company branches into the larger corporate networks. We can also thank ciphers for protecting data privacy in most Wi-Fi networks, online banking and e-commerce, and communications through our cell phones.
Interested in learning more about Masonic history and symbols? Explore our blog on Masonic Coins and Tokens.
Have you seen the Masonic Cipher used in modern times? If so, tell us about your experience on social media by tagging @GrandLodgeOhio on Facebook and Twitter.